
International Day of Families at HENSOLDT Cyber
International Day of Families at HENSOLDT Cyber Interview with Markus Wolf, Sascha Fedderwitz, Emilia Fries We asked some of our colleagues a few questions on

Written by Maja Malenko, Hardware Researcher at HENSOLDT Cyber
Creating secure hardware is a challenging task, especially in times of very diverse and prominent hardware attacks. MITHRIL supports the development of highly secure and trusted hardware (EU initiative) through the improvement of multiple aspects of hardware security.
Is hardware really secure?
Hardware plays the most important role in a system’s security and trust. It enables, enhances, and enforces security. However, if the hardware is not designed and implemented properly (with security in mind), it becomes a system’s weakest security point. In contrast to other security domains (e.g., software and network security), hardware security is a fairly young field. Until very recently, hardware was considered inherently secure and unbreakable. Not any more.
The dawn of hardware attacks started with fault injection attacks on smart cards. Then side-channels on earlier cryptographic implementations became attractive. The transition from vertical to horizontal business models in the IC supply chain opened the doors to a new class of attacks, where design houses may no longer have full control over their products. Today, hardware’s role as a trust anchor is challenged.
This blog post is the first of three in a series on hardware security, in which we give a brief overview on hardware attacks. HENSOLDT Cyber’s MITHRIL (Maßnahmen der IT-Sicherheit zur Hochsicheren HardwaRe IndustriaLisierung) project aims to contribute to the initiative for highly secure hardware industrialization by analysing and evaluating the security of embedded hardware and software but moreover, by defining security requirements and creating a prototype that can be resilient against many attacks discussed below.
Who is the attacker?
When talking about attacks, we must discuss the attack model first, i.e., the attacker’s intentions and capabilities. The final goal of every attack is either stealing or manipulating sensitive information (e.g., cryptographic keys, configuration, user data), or controlling the device, making it malicious or even non-functional. The motive behind these attacks might be financial gain, espionage, state security, sabotage, competitive analysis, and might even result in impacting people’s lives, especially in the embedded domain (e.g., medical equipment, automotive, aerospace, military, smart things, critical infrastructure). Mindful hardware manufacturers face a trade-off between cost and security of their products. By knowing the attack model, they can put different countermeasures in place. Hardware attacks can take many different forms: remote or physical, invasive or non-invasive, triggered by and targeted towards both hardware and software. The software and each component of the Integrated Circuit (IC) can be part of the attack surface including CPU, memory, internal and external buses, clock and power supplies.
The famous RowHammer attack was triggered by malicious software targeting faults, i.e., bit flips in memory. A single bit flip can have a huge impact on the security of a device, circumventing security checks like signature verification and password authentication. Similar fault-injection attacks can be triggered by hardware as well (e.g., laser attacks).
Trust issues in the IC supply chain
The majority of semiconductor companies cannot afford their own fabrication facilities. In the last two decades, pressured by time-to-market and manufacturing costs, they have shifted towards a horizontal business model and have outsourced parts of the design process as well as the fabrication, testing, and packaging phases.
As a result of the involvement of potentially untrustworthy entities in the hardware lifecycle, including IP providers, CAD tool vendors, foundries, as shown in figure 1, security and by extension safety concerns have emerged: reverse engineering, malicious hardware modifications, IP piracy and counterfeiting, etc.
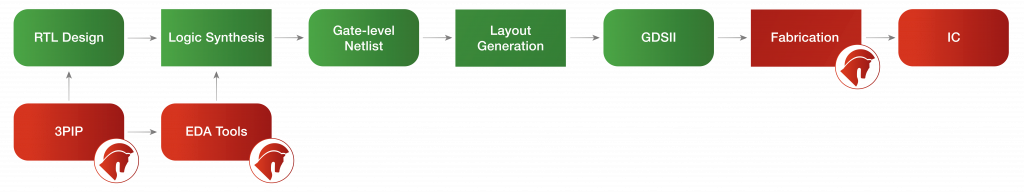
Figure 1: Potentially untrustworthy entities in the IC supply chain. Image copyrights: HENSOLDT Cyber
Types of hardware attacks
Hardware attacks can have different types. Let’s look at the four most common ones as shown in figure 2. The goal of a reverse engineering attack is to determine the structure and functionality of the IC. In order to get to the netlist, which is a sea of connected gates representing the logic of the design, the end user must go through an expensive and error-prone process of depackaging, delayering, and imaging. Foundries, however, may abuse their access to the design layout, rendering this process much easier and effective. From there, many different techniques can be used to analyse the netlist and identify its functionality. The motivation for reverse engineering can be malicious modification of the circuit, piracy, or understanding the competitors.
Hardware Trojans are intentional and malicious modifications of the circuit that results in an undesired behaviour when the circuit is deployed. They can be inserted by third-party IP providers, CAD tool vendors or untrustworthy foundries. Trojans in cryptographic engines can leak secret keys, and if inserted into CPUs they can skip the memory protection mechanisms to gain privileged access. While real Hardware Trojan attacks have not been officially reported, they have raised severe concerns regarding possible threats to military systems, transportation security, financial infrastructures.
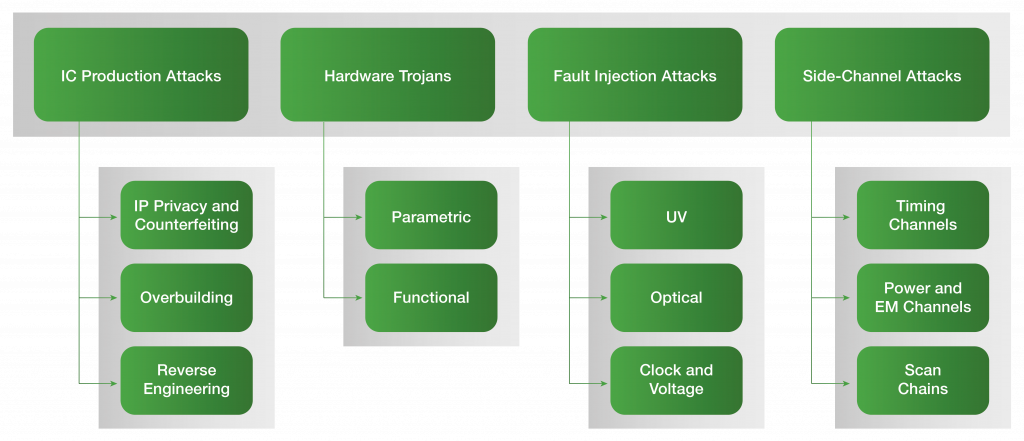
Figure 2: Types of hardware attacks. Image Copyrights: HENSOLDT Cyber
The goal of a fault injection attack is to force abnormal system operation using physical or software methods. These attacks are typically combined with other hardware attacks to gain unauthorized access or learn secret data. Unlike faults that naturally occur in the circuit (e.g., radiation-induced faults) and lead to safety and resilience issues, attacker-induced faults are intentional, which means they are artificially produced and exploitable.
Side-channel attacks (SCAs) are the most successful attack on modern cryptography systems, targeting their implementations, both in hardware and in software. They aim at extracting secret information through measurements and analysis of side-channels, including timing behaviour of hardware or memory subsystems, power and electromagnetic emission, scan chains, etc. A large number of hardware and software optimizations are vulnerable to SCAs (e.g., naive square-and-multiply algorithm for modular exponentiation, speculative execution, branch prediction, memory optimizations, etc.).
In a two-week rhythm, we will publish our next blogposts on hardware security. We will focus more on the specific types of hardware attacks to give you a little insight into what’s coming next. Stay tuned!

International Day of Families at HENSOLDT Cyber Interview with Markus Wolf, Sascha Fedderwitz, Emilia Fries We asked some of our colleagues a few questions on

How to mitigate hardware attacks? Written by Maja Malenko, Hardware Researcher at HENSOLDT Cyber In the final blog post of our hardware security trilogy, we

Is Hardware Reverse Engineering a Real Threat? Written by Maja Malenko, Hardware Researcher at HENSOLDT Cyber Today we are continuing the story of hardware security

Hardware Security: HENSOLDT Cyber’s MITHRIL Project Written by Maja Malenko, Hardware Researcher at HENSOLDT Cyber Creating secure hardware is a challenging task, especially in times

Successful ISO 9001:2015 certification We are pleased to announce that after eight months of hard work, preparation, and intensive teamwork, HENSOLDT Cyber has certified its

Hello Secure World – How to build and run your first secure TRENTOS® system Building on our first video session in which we took a
LEGAL:
CONTACT US:
FOLLOW US ON:
HEADQUARTER POSTAL ADDRESS:
OUR OFFICE IS LOCATED HERE: